
What is SOC 2?
SOC 2 sets five criteria of data security that apply to any businesses storing its client data in the cloud. This includes almost every outsourced IT vendor. The SOC 2 audit confirms the business’s ability to implement and maintain proper data security procedures.
For any business that handles client data, it is becoming increasingly important to achieve and maintain SOC 2 compliance to show you have adequate security measures and controls in place.
How to Get Started With SOC 2 Compliance:
Your Complete IT Security Guide
Need help with SOC 2 compliance? We've compiled everything you need to know!
Which level of SOC 2 certification do you need?
For most organizations looking to achieve SOC 2 compliance for the first time, Type 1 should be the goal. However, the ultimate goal is to become Type 2 certified.
So, what’s the difference?
SOC 2 Type 1 – Assesses the suitability of the business’s security controls and how well they match SOC’s five criteria.
SOC 2 Type 2 – Assesses the effectiveness of the business’s security controls over a minimum 6-month period.
What are the main components of SOC 2 compliance?
To become SOC 2 Type 1 or Type 2 compliant, it is essential to follow the five Trust Services Criteria (TSC):
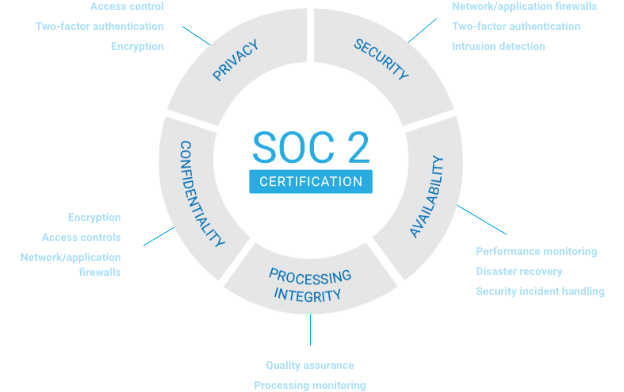
Systems are protected against unauthorized access by firewalls and other access controls.
Systems are backed up and monitored, with clear recovery protocols in place.
Data is categorized and protected by encryption and access controls like MFA.
Processes are complete, accurate, timely, and meet organizational objectives.
Personal information must be collected, used, disclosed, and disposed of in a secure manner.
Achieve SOC 2 compliance with
our simple 3-step process:

Gap Assessment
A Gap Assessment shows how well you are following the five Trust Services Criteria. It will identify any weaknesses in your security posture and recommend ways to strengthen them.
Once any weak points are revealed, we will develop an easy, economical solution plan. Whether you are looking to achieve a Type 1 or Type 2 certification, a Gap Assessment will ensure there are no surprises come audit time.
Enlist our SOC 2 services
Backup and Disaster Recovery
Backup and Disaster Recovery
Dark Web Monitoring
Dark Web Monitoring
Endpoint Encryption
Endpoint Encryption
External Vulnerability Scanning
External Vulnerability Scanning
Security Awareness Training
Security Awareness Training
SIEM
SIEM

SOC Audit Assistance
Preparing for a SOC 2 audit is daunting, and we are here to help.
Charles IT will guide you through the process by recommending SOC 2 auditors and then acting on your behalf to produce the evidence needed to prove your security posture and effectiveness of controls.
Do not let this process distract you from what you do best: running your business. Let Charles IT step in and help you on the path to SOC 2 certification!
What results to expect
Once we start working with clients to achieve SOC 2 certification, we see them enjoy…
- Confidence in passing the SOC 2 audit
- Robust cybersecurity and disaster recovery protocols
- Increased client trust from better data management
- Peace of mind that they are secure and SOC-compliant
Don't just take our word for it
It’s always a great feeling when you know that someone has your back. Thanks for the fast response time and professional service, Matt!
Charles IT are ALWAYS so responsive and helpful. Truly the best!
Charles IT are always thinking of everything we’re not. They listen to our needs and they don’t just point out problems, they have solutions.

