CMMC 2.0 CERTIFICATION: EVERYTHING DoD CONTRACTORS NEED TO KNOW TO ADHERE TO REVISED PRIVACY STANDARDS

Introduction
It’s been said that the only thing that’s constant is change. This is definitely true when it comes to the world of cybersecurity.
If you’re an existing DoD contractor, then you’ve hopefully achieved Defense Federal Acquisition Regulation Supplement (DFARS) compliance and are familiar with the Cybersecurity Maturity Model Certification, or CMMC, framework.
But did you know that the DoD has drastically revised their requirements with the introduction of new CMMC 2.0 standards?
As the threat landscape continues to evolve, hackers and scammers grow bolder to obtain confidential data. Cybercriminals have targeted and continue to target the Defense Industrial Base (DIB) sector, as well as the Department of Defense’s (DoD) supply chain in the hopes of stealing vital intellectual property and sensitive information.
This climate prompted the DoD to create the original CMMC framework to bolster security, and subsequent feedback from stakeholders initiated the creation of the new CMMC 2.0 model. Reactive measures are no longer enough to protect your organization and the data in its care. The new framework is a certification procedure designed to assure the DoD that DIB contractors are capable of protecting sensitive information such as Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
What Does the Change to CMMC 2.0 Mean for Your Company?
For one thing, it means that the time to begin preparing is now. Any business that contracts with the DoD or subcontracts with a business that sells to the DoD must achieve compliance soon.
The DoD has stated that CMMC 2.0 will not be a contractual requirement until the Department completes rulemaking to implement the program. Since the announcement of CMMC 2.0 in November of 2021, the DoD has since maintained that the CMMC 2.0 rulemaking process could take anywhere from 9-24 months.
In fact, a recent Inside Cybersecurity article cites DoD Director of CMMC Policy, Stacy Bostjanick, who stated, “We are thinking, hoping and praying that by next March we will be approved to get an interim rule. There will be a 60-day comment period which will put us at the end of May 2023.” If that timeline holds, contractors have no time to waste.
Further cementing the forward progress, Inside Cybersecurity announced that The Cyber AB began the first official CMMC 2.0 assessment on August 22, 2022, under the Pentagon’s “joint surveillance voluntary program,” where a Certified Third-Party Assessment Organization (C3PAO) will conduct the examination and report results to the Defense Contract Management Agency for final approval. These assessments are being led by accredited C3PAOs with supervision from Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) and will convert into CMMC 2.0 assessments upon completion of CMMC Rule Making, expected in March 2023.
For many organizations, contracts with the DoD make up a significant part of their revenue. If your company is audited by the DoD and found to be noncompliant, you will be given a stop-work order until your company can implement sufficient security measures to keep CUI protected. The DoD can also impose fines on contractors for breach of contract and false claims.
Compliance is also worthwhile for organizations that don’t currently work for the DoD since it can open up new business opportunities in the future. It’s also worth noting that DoD CMMC 2.0 is one of the most comprehensive cybersecurity compliance regimens currently in place, so it’s a great way to establish an organization’s authority in cybersecurity.
Making this transition can be overwhelming – but it doesn’t have to be. That’s why we’ve created this guide to explain everything you need to know in order to be prepared for CMMC 2.0 compliance.
Back to top

01
When Does CMMC 2.0
Take Effect?
By now you’re probably familiar with the original CMMC framework. Now that the DoD has rolled out a new version of CMMC to replace the former CMMC 1.0 requirements, you may be wondering how it will affect your business.
With the CMMC 2.0 compliance deadline quickly approaching, DoD contractors have a short window to prepare for compliance.
It’s important to note that, in the meantime, the new CMMC 2.0 requirements don’t replace DFARS regulations. In fact, every DoD contractor that deals with CUI still runs the risk of losing their contracts if they do not comply with the minimum security requirements of DFARS.
According to current guidance from the DoD, CMMC 2.0 will require 9 to 24 months of rulemaking. Their website specifically states that “the interim DFARS rule established a five-year phase-in period, during which CMMC compliance is only required in select pilot contracts, as approved by the Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S)).
The Department does not intend to approve inclusion of a CMMC requirement in any contract prior to completion of the CMMC 2.0 rulemaking process.”
Organizations can prepare now by implementing NIST 800-171, which is already present in contracts as DFARS 252.204-7012. By implementing NIST 800-171, you can improve the self-assessment score you post to the DoD’s Supplier Performance Risk System (SPRS). The DoD also indicates that there will be incentives for improved scores and/or early adoption of CMMC 2.0.
The Evolution of CMMC: A Look Back
In 2020, the DoD moved to require contractors to adhere to CMMC version 1.0, which was a supplement to DFARS 7012—the set of regulations currently used by the DoD to regulate Controlled Unclassified Information (CUI). CMMC 1.0 was not meant to replace DFARS 7012, but rather to augment adherence to it by eliminating self-certification and replacing it with third-party certification. The creation of CMMC model 1.0 was, in fact, part of the effort to improve the low rate of DFARS compliance.
However, the DIB received numerous comments and recommendations upon their first ruling of CMMC 1.0. Critics noted that it placed undue burden on SMBs, who were forced to navigate high costs of third-party assessments and complex requirements that didn’t have a direct correlation with standards set forth by the National Institute of Standards and Technology (NIST). Other problems indicated were centered around a lack of oversight of ethical practices by third-party assessors.
Another objective of the revision was to reduce the costs of certification. The DoD will publish a comprehensive cost analysis associated with each level of CMMC 2.0 as part of rulemaking on their website. They report that costs are projected to be significantly lower, relative to CMMC 1.0, as a result of streamlining efforts.
Alignment with DFARS
Understanding CMMC 2.0 first means that you should have a firm grasp on how DFARS and CMMC align. DFARS and CMMC 2.0 are similar in many ways (because the latter draws heavily from the former). Unlike DFARS, CMMC 2.0 has three levels of maturity with each level characterized by its focus.
To be DFARS-compliant, a DoD contractor must meet 14 control families, within which are 110 controls stipulated in the National Institute of Standards and Technology Special Publication (NIST SP) 800-171.
Alternatively, CMMC 2.0 uses different technical frameworks for each level. By categorizing its contractors into one of three levels, the DoD can ensure that contractors for each project have the appropriate cybersecurity practices and processes in place to protect FCI and CUI.
CMMC 1.0 vs. CMMC 2.0: Key Differences
The CMMC version 2.0 is a revision to the prior set of regulations. Businesses contracting with the DoD are required to acquire a certain certification level representing their cybersecurity maturity.
The new model changes the process significantly:

Fewer Levels
CMMC 2.0 now uses only three levels of maturity, rather than the previous five levels, to identify an organization’s cyber maturity: Foundational, Advanced, and Expert. (The new model collapses the previous transitional levels 2 and 4.) Once CMMC 2.0 is implemented, the DoD will specify the required CMMC level in contract solicitation and in any Requests for Information (RFIs). Businesses that deal with or generate CUI will need at least a Level 2 CMMC certification—we’ll explain more about the levels of certification in chapter 3.

Elimination of Processes and Practices
CMMC 2.0 has eliminated the former processes specified in CMMC 1.0, as well as all “CMMC unique” practices. However, anytime you make claims about your organization’s cybersecurity environment to the DoD, it is beneficial to document policies and processes to clearly define structure and ensure those statements are verifiable.

Self Assessments
DoD contractors seeking Levels 1 certifications will no longer require third-party certification. However, contractors seeking Level 2 Advanced Certification can expect to be accredited every three years by C3PAOs or certified CMMC Assessors. Contractors working on highly sensitive programs will need to reach Level 3 Expert compliance and obtain a special audit from the Defense Contract Management Agency’s Defense Industrial Base Cybersecurity Assessment Center.

Annual Affirmations
CMMC 2.0 calls for an annual affirmation from a senior company official. The Department of Justice (DOJ) announced an intent to hold entities or individuals accountable that knowingly misrepresent their cybersecurity practices. It’s wise for contractors to begin defining their process for completing this step and identifying the individual who should sign the affirmation.

Plan of Action and Milestones (POA&Ms) and Waivers
Contractors that are not yet in full compliance with specified cybersecurity requirements can be permitted to perform less sensitive contracts. In order to do so, contractors must submit a POA&M outlining the specific tasks to be completed, the date that they will be achieved, and all resources that will be used for remediation. The DoD will provide a ruling on their time limits that will apply to these cases and is currently considering a 180-day timeline from contract award for companies to meet the measures laid out under their plans.
Who Needs to Be CMMC 2.0 Compliant?
All prime contractors and subcontractors working for the DoD should be CMMC 2.0 compliant. A prime contractor is a company that works directly with the DoD and needs a high-level certification. A sub-tier supplier is a company that is subcontracted by a prime contractor to work on projects relevant to the supply chain.
If contractors and subcontractors are handling the same type of FCI and CUI, then the same CMMC level will apply. In cases where the prime only shares select information with subs, a lower CMMC level may apply to the subcontractor.
A contractor’s access to CUI will also determine the level of certification needed. If a contractor doesn’t handle or manage CUI, but works with federal contract information (FCI), the contractor should comply with Federal Acquisition Regulation (FAR) Clause 52.204-21 and should be at least CMMC 2.0 Level 1 compliant.
CMMC Third Party Assessor Organization (C3PAOs), Training Providers, Instructors and Assessors
The CMMC Accreditation Body (CMMC-AB) responsible for accrediting third-party assessment organizations has rebranded to become, “The Cyber AB.” The Cyber AB operates under an exclusive contract with the DoD that charges and authorizes the organization to serve as the sole provider of CMMC licensing and certification for C3PAOs, training providers, instructors, and assessors.
In late 2021, The Cyber AB provided an endorsement of the Pentagon’s proposed implementation changes in CMMC 2.0, acknowledging the designation of CMMC Level 1 as a self-attestation requirement only.
The DoD is coordinating with The Cyber AB to develop the current “assessment ecosystem.” In June of 2022, The Cyber AB launched the Academic Advisory Council (AAC), created “to facilitate a critical voice from higher education institutions to provide key feedback and recommendations for successfully implementing CMMC in an academic environment.”

A C3PAO is authorized (and in the future accredited) by The Cyber AB to contract and manage CMMC assessments. Contractors can only be audited and certified once the C3PAOs have been trained with the CMMC accreditation body (AB). Once accredited, these auditors can perform CMMC assessments and grant eligible contractors CMMC certifications. The Cyber AB maintains a list of C3PAOs on its website.
The process to become a C3PAO is intensive. Once the Cyber AB confirms the Candidate C3PAO is ready to be assessed by DIBCAC, their information is forwarded to the DoD CMMC PMO, who is responsible for scheduling the CMMC Level 2 Assessment by DIBCAC. C3PAOs become authorized to conduct assessments upon achieving CMMC Level 2, meeting the various administrative requirements (e.g., proof of insurance, dispute resolution process, etc.), and, ultimately, receiving their “Authorized C3PAO Badge” from The Cyber AB.,

A CMMC Provisional Assessor is an individual who was randomly selected from the Assessor applicant pool to participate in the CMMC pilots. Assessors can affiliate with as many C3PAOs as they like.

A Certified CMMC Instructor, or CCI, is an individual responsible for teaching the CMMC framework to candidates seeking to be an assessor.

A Licensed Training Provider (LTP) is an established training organization that has been vetted by the CAICO to be approved as an LTP. To maintain their status LTP, an individual must deliver at least one certified class per year. In addition, certified classes must use The Cyber AB Approved Training Material (CATM) and be taught or facilitated by The Cyber AB Certified Instructors.
Back to top

02
CMMC 2.0, DFARS and NIST: A Closer Look
To further prepare for challenges ahead, realize that CMMC 2.0 does not put an end to DFARS. In fact, every DoD contractor that stores, processes, and transmits CUI runs the risk of losing their contracts if they fail to comply with the minimum-security requirements of DFARS. To be considered DFARS-compliant, a contractor needs to fulfill the requirements of NIST SP 800-171, which involves 110 controls.
The CMMC 2.0 Level 2 certification requires fulfillment of all 110 practices identified in NIST SP 800-171.
Level 3 contractors must meet the requirements of NIST SP 800-171, plus a subset of requirements specified in NIST SP 800-172. The DoD is still in the process of determining how organizations seeking level 3 compliance will be assessed.
What is NIST 800-171?
NIST 800-171 is a NIST Special Publication that details requirements for protecting CUIs.
How NIST 800-171 Relates to the NIST Cybersecurity Framework (CSF)
NIST created the Cybersecurity Framework, or CSF, as a voluntary set of standards, guidelines, and best practices for managing cybersecurity risk. While providing a comprehensive and standardized approach to managing cybersecurity risks for all businesses, NIST CSF is also a key tool for complying with various regulations and standards, like DFARS and CMMC. NIST 800-171 falls under the umbrella of NIST CSF and applies specifically to defense contractors and those dealing with CUIs.
The CMMC 2.0 model is based on the 14 NIST 800-171 Compliance Control families:
- 1. Access Control
- 2. Audit and Accountability
- 3. Awareness and Training
- 4. Configuration Management
- 5. Identification and Authentication
- 6. Incident Response
- 7. Maintenance
- 8. Media Protection
- 9. Personnel Security
- 10. Physical Security
- 11. Risk Assessment
- 12. Security Assessment
- 13. Systems and Communications Protection
- 14. System and Information Integrity
1
Access Control
Access control focuses on the process of allowing or denying a user’s request to enter company facilities, use CUI, and make use of information processing services. System-based access controls, also known as logical access controls, determine who should be given access to system resources and the type of access permissions.
For instance, users should only be given access to the information and resources they need to perform their tasks, and access to non-job-related information should be prohibited. In addition, the type of access permission such as read and execute, read only, write, and full control should also be limited to prevent unauthorized access to CUI.
2
Audit and Accountability
Employees are considered one of the weakest links in a company’s cybersecurity defense. Oftentimes, workers are unaware of how their actions impact the security of the company infrastructure. For example, a user who can’t identify a phishing email may end up clicking on a compromised link that installs malware or takes that user to a fake site designed to steal sensitive information. Raising cybersecurity awareness and providing regular training will help employees understand their security responsibilities and instill best practices in identifying various cyberthreats.
3
Awareness and Training
DoD contractors are required to create, retain, and protect system audit records to monitor, analyze, investigate, and report all unauthorized, unlawful, and inappropriate activities associated with CUI. These records can help trace specific user actions to find whoever carried out the unsanctioned activities and hold them accountable in case CUI is leaked or compromised.
4
Configuration Management
Configuration management is a group of activities designed to maintain the integrity of information technology systems and products by controlling the configuration process. It involves identifying and documenting the correct system settings, performing a security impact analysis, and managing all changes using a change control board.
Without proper documentation, you wouldn’t know if changes made to one system would have an adverse effect on another business-critical system. This lack of insight can prevent your employees from performing their tasks, or worse, leave your infrastructure open to cyberattacks that can compromise CUI.
5
Identification and Authentication
This control family identifies users requesting access to CUI and authenticates their identity before being granted access to CUI and other system resources. It is a vital part of cybersecurity because it acts as a first line of defense that prevents unauthorized people from accessing your system.
Apart from securing the initial login process, an effective identification and authentication system is also able to track whether an authenticated user is still active within the system. For instance, a user who is no longer using a terminal or has been inactive for some time is automatically logged off. This prevents unauthorized people from using that same terminal that might have access to CUI.
6
Incident Response
An incident response plan allows your organization to react to emergency events such as natural disasters, cyberattacks, and utility outages. Critical to an incident response plan is a solid backup and recovery strategy, which allows you to restore data from a recent version if necessary. For example, an important file that was accidentally deleted by a user or corrupted because of a malware attack can be restored from a backup.
Without an incident response plan, emergency events can quickly spread, leading to escalated damage and serious harm to your company. An effective incident response strategy should contain sufficient preparation, detection, analysis, containment, recovery, and user response activities. These incidents should be tracked, documented, and reported to management and/or internal and external authorities.
7
Maintenance
Implement system maintenance procedures that will ensure your infrastructure is working properly and prevent software and hardware failures. There are various ways to do this. Controlled maintenance refers to scheduled maintenance conducted based on a manufacturer’s specifications. Corrective maintenance, on the other hand, is performed when a system or part of a system fails. Improper system maintenance or failure to conduct one can lead to the unauthorized disclosure of CUI, which can compromise its privacy and confidentiality.
8
Media Protection
This control family focuses on the protection of system media, both digital and non-digital. Examples of digital media include external or removable hard drives, compact discs, magnet tapes, and flash drives. Examples of non-digital media include microfilm and paper.
There are several ways to ensure media protection. First, access to CUI or other resources contained in system media should be limited to authorized personnel only. Employees should also be able to use only digital media approved by an asset manager to store CUI. Policies should be implemented on how to remove CUI from media so that the information cannot be reconstructed or retrieved once the media is released for reuse or destroyed. Media protection also includes limiting the use of personal mobile devices capable of storing information inside restricted areas.
9
Personnel Security
Since DoD contractors work with proprietary and sensitive information, accidental or intentional disclosure of that information can result in financial and reputational damage. This is why contractors should be extra careful when hiring new workers and reassigning or terminating employees. An extensive background check and screening process must be conducted before hiring new employees to ensure they pass established security criteria and are trustworthy.
Employees who are transferred or reassigned should be given a new set of system and physical access permissions, while their old ones are returned or disposed of properly. Terminated employees must have their access disabled, and the employers should also retrieve all system-related property and information used by the terminated employees.
Personnel security aims to reduce the risk that employees pose to CUI and other company assets through the exploitation or malicious use of their access to organizational resources.
10
Physical Security
Physical protection refers to the measures taken to protect buildings, systems, and supporting infrastructure from threats related to their physical environment. Sensitive areas in your facility should implement safeguards such as security guards, closed-circuit television cameras, locks, and card readers so that only authorized personnel can access these areas, ensuring CUI security and safety.
In addition, contractors must ensure their facility is safe from natural disasters, man-made threats, and damaging nearby activities such as civil disorder, and electromagnetic interference to prevent or minimize disruptions to your operations.
11
Risk Assessment
Risk assessments can identify and prioritize risks to your company’s assets, operations, employees, and partners. It will help you create effective remediation strategies to address various security-related issues such as supply chain attacks and advanced persistent threats. For instance, it can help you defend your systems from vulnerabilities brought about by the implementation of new technologies.
12
Security Assessment
A security assessment tests and/or reviews your company’s operational, management, and technical security requirements. These tests ensure that business components have been implemented correctly, are operating properly, and are producing the desired results based on your infrastructure’s security requirements. Just like in a risk assessment, you must create a plan of action to address deficiencies and minimize or eliminate any vulnerabilities in your current security policies.
13
Systems and Communications Protection
This control family focuses on the confidentiality of CUI at rest and in transit. System and communications protection creates barriers that limit access to publicly accessible information within your system. It also lets you monitor and control communications at internal and external boundaries to prevent unauthorized transfer of CUI. Additionally, CUI must be encrypted before transit to prevent unauthorized modification and disclosure.
14
System and Information Integrity
System and information integrity ensures that the CUI being accessed has not been tampered with or damaged by a system error. It requires contractors to identify, report, and correct system flaws in a timely manner. Contractors must also take the appropriate measures to protect their infrastructure from malicious codes that can compromise the integrity of CUI. This includes installing antivirus software, updating software and applications, and monitoring and addressing security alerts.
Though many of these controls can be aided by third-party technological solutions and sealing the gaps in your IT environment, not all the requirements have such a straightforward solution. Many of the controls require process change, including documentation of new policies, processes, and procedures. Some controls address security awareness training issues and the measures in place to secure the physical environment.
Back to top

03
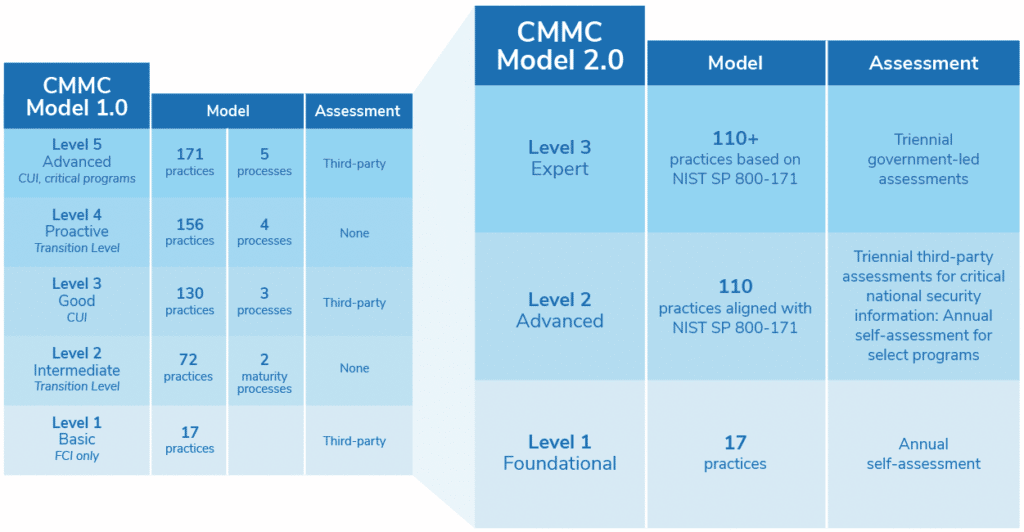
CMMC 2.0 Levels
As we’ve established, CMMC 2.0 operates on a framework that aligns with existing DFARS requirements. It consists of three levels that DoD suppliers mature into as they get better at protecting federal contract information (FCI) and CUI. Particularly, each CMMC maturity level is characterized by a set of cybersecurity practices.
Why the Tiered Approach?
Before the CMMC was created, contractors who wanted to work for the DoD were expected to comply with NIST SP 800-171. However, small and medium-sized businesses (SMBs) found it difficult to achieve compliance with the full control set because they had neither an in-house IT staff nor a dedicated information security expert. This made reaching even basic cybersecurity hygiene difficult.
Larger companies, on the other hand, found it easier to achieve full NIST SP 800-171 compliance because they were held to more rigorous standards such as the Federal Risk and Authorization Management Program (FedRAMP) standard and NIST’s Cybersecurity Framework (CSF). However, for these larger contractors, NIST SP 800-171 presented a financial disadvantage when it came to implementing continuous improvements. Once they achieved the minimum baseline, larger contractors found no reason to invest more resources in their information security posture.
The CMMC 2.0 model addressed these concerns by using a tiered approach. Each control stated in NIST 800-171 is assigned to a specific maturity level, with Level 1 being the most basic and Level 3 being the most stringent. The levels and their associated cybersecurity practices are cumulative. This means that to be certified at a certain CMMC level, you must meet all the requirements of the preceding levels as if you’re applying for certifications for all of those levels. This allows applicants to apply for a certification level of their choosing once, rather than having to go through certifications multiple times.
For example, to get CMMC Level 2 certification, you must satisfy the cybersecurity requirements for both Levels 1 and 2. What’s more, you must demonstrate the cybersecurity practices associated with Level 2.
Each CMMC level also has a particular focus to ensure alignment between cybersecurity practices with the type and sensitivity of information to be protected. Only companies that achieve CMMC Levels 2 and 3 can handle CUI, with Level 3 offering increased protection against advanced persistent threats (APTs).
On the other hand, those that get Level 1 certification need to secure only FCI, which means they don’t need to meet full DFARS compliance. This makes certification more cost-effective and affordable to smaller DoD vendors that don’t deal with CUI. Now, let’s take a closer look at each CMMC 2.0 level
CMMC 2.0 Level 1: Foundational Cyber Maturity
Guided by the Federal Acquisition Regulation (FAR), this is the minimum level of cyber hygiene required to hold Federal Contract Information (FCI), beyond the DoD. A level 1 certification indicates that cybersecurity best practices concerning the identified controls are “performed” and included in the business’s processes.
This is the easiest of the three levels to achieve, and contractors may self-certify.
CMMC 2.0 Level 2: Advanced Cyber Maturity
Any company working with CUI should aim for this level. It is comparable to the former CMMC Level 3. These requirements are in complete alignment with NIST SP 800-171 practices. All practices and maturity processes that were unique to CMMC 1.0 have been eliminated, which means that the 20 requirements in the old CMMC Level 3 that the DoD had imposed were dropped. Now, Level 2 directly correlates with the 14 levels and 110 security controls developed by the National Institute of Technology and Standards (NIST) to protect CUI.
CMMC 2.0 Level 3: Expert Cyber Maturity
Contractors at this level are required to focus on reducing the risk from Advanced Persistent Threats (APTs). This level is exclusively for companies working with CUI on DoD’s highest priority programs. It is comparable to the old CMMC Level 5. The DoD has indicated that its requirements will be based on NIST SP 800-171’s 110 controls plus a subset of NIST SP 800-172 controls. These should be met before undergoing a triennial government-led assessment. The DoD, however, is in the process of developing the requirements for this level, which is still undergoing change.
As a DoD contractor, you should identify your organization’s cyber security level based on the classification of the data you store, transmit, and process. Your IT team must be familiar with NIST SP 800-171 and the appropriate target levels so that they can determine the right CMMC 2.0 controls to adopt for your organization.
Understanding how you can prepare the transition to CMMC 2.0 compliance is a must no matter what cyber security level you are aiming for. This is where experienced professionals can be a tremendous asset.
Let’s examine further.
Back to top

04
Preparing for CMMC 2.0 Compliance
Once you gain an understanding of the CMMC 2.0 certification levels, it’s time to look toward preparing for an audit. All DoD contractors should prepare for a CMMC audit, even for a Level 2 certification. A self-assessment is an excellent way to pinpoint issues in a contractor’s cybersecurity program that should be addressed before the audit. Contractors should focus on the controls found in NIST SP 800-171 Rev. 1. Once these controls are in place, you can easily obtain a Level 2 certification.
7 Steps to Take Now
Use this checklist to make sure your company is on track in
preparing for a CMMC audit and achieving compliance.

Define CUI Specific to Your Contract
The first step you need to take is to indicate your company’s CUI environment. This is a controlled environment where CUI is stored, processed, and transmitted. It’s important to know what the CUI environment is because it defines the processes, services, and systems in scope for NIST SP 800-171. If you’re not sure what your CUI is, you can ask for assistance from your contracting officer.

Identify Applicable NIST 800-171 Controls
For CMMC 2.0 Level 2, you must identify which controls apply to your CUI environment from 61 NFO and 110 controls.

Create Policies and Processes to Meet Cybersecurity Compliance Requirements
Even though CMMC 2.0 has eliminated the requirement for processes, it’s still wise to complete this step. Identify all applicable contracts, regulations, laws, and requirements with which your company should comply, and create policies and processes that will help you meet and manage those requirements. These policies must be concise and directly align with your company’s compliance requirements.

Operationalize Your Policies to Implement CMMC / NIST 800-171 Controls
This is where your technology, processes, and people come together to operationalize your privacy and cybersecurity program. It implements the exact requirement for compliance and brings your policies to life. This step requires you to identify teams responsible for specific CUI controls and define their roles and responsibilities to ensure requirements are properly implemented.

Create a Documentation of Your CUI Environment
Create a Plan of Action & Milestone (POA&M) and a System Security Plan (SSP) to document the changes that affect your CUI environment. These two documents are important for two reasons:
- The SSP contains information about the processes, people, and technologies used to manage your CUI environment.
- The POA&M acts as a risk register for deficiencies in NIST 800-171 controls.
Also, a CMMC auditor needs your SSP and POA&M to properly assess your CUI environment. These documents are also required for NIST 800-171 compliance. If your company lacks these documents, you risk non-compliance penalties.

Use the Controls to Assess the Maturity and Risks of Your Business and Technology Processes
There are various methodologies available your organization can use to manage risk. There are risk models from ISO 31010, FAIR, OCTAVE, and NIST 800-171 that assess how effective controls are implemented and how much risk is reduced based on the control’s level of maturity. However, there’s no perfect risk methodology, and you should choose one that best supports your company’s functions.
It’s even possible to use different risk methodologies for operational, strategic, and tactical risk decisions because each has its own strengths and weaknesses. The goal of this step is to allow your company to define and achieve a level of optimal risk-taking.

Identify Areas for Improvement Using Metrics From Control Execution
Gathering metrics gives you a snapshot of a control’s performance and helps you identify areas for improvement. You can do this by defining key risk indicators (KRIs) and key performance indicators (KPIs) to gain insight into the controls vital to your organization.
Determine Your Desired CMMC 2.0 Level
Contractors and subcontractors working in an unsecured email environment leave themselves open to the most common way hackers steal data — phishing. According to Cybersecurity Magazine, about 43% of cyberattacks target small and mid-sized businesses, including DoD contractors, and 85% of MSPs consider ransomware one of the biggest threats to their SMB clients.
As such, some DoD contractors and subcontractors are looking to the cloud to increase their cybersecurity measures against phishing attacks. This is where understanding the Federal Risk and Authorization Management Program (FedRAMP) and Microsoft Government Community Cloud (GCC) High comes in.
What is FedRAMP?
The Federal Risk and Authorization Management Program (FedRAMP) is important for cloud service providers that serve federal agencies. It was developed by the National Institute of Standards and Technology (NIST), the General Services Administration (GSA), the Department of Defense, and the Department of Homeland Security (DHS).
FedRAMP is a program developed by the United States government to standardize cloud services providers’ and similar organizations’ security assessment, authorization, and continuous monitoring processes for their cloud products and services. It’s primarily concerned with ensuring that public cloud systems containing federal data are well-protected.
FedRAMP ensures that government entities use adequately safeguarded cloud systems, reduce risk management costs, and procure information systems and services rapidly and cost-effectively. Moreover, FedRAMP builds on the Federal Information Security Management Act (FISMA), a law that requires federal agencies to develop, document, and implement an information security and protection program that abides by the E-Government Act Law of 2002.
Here are the steps you need to take to achieve FedRAMP compliance:

Step 1:
Document
This involves categorizing the information system or service under consideration based on the “Standards for Security Categorization of Federal Information and Information Systems” of the NIST publication FIPS-199. Categorizing the data that will be processed within the information system is key to identifying the impact level (low, moderate, or high) of the cloud service or product in case of a security breach. The impact level will then determine the type of data that the provider will be authorized to handle.
Key Points

The selected impact level indicates which NIST 800-53 and FedRAMP controls must be used to comply with the program’s requirements.

A CSP can complete a FIPS PUB 199 Worksheet via www.fedramp.gov.
Step 2:
Assess
A third-party assessment organization (3PAO) steps in to examine the effectiveness of the implemented controls. They will conduct a security assessment on the actual system (i.e., not a test system) to be used.
Key Points

CSPs are not required to use a FedRAMP-accredited 3PAO. However, any independent assessor must create a testing plan that utilizes the FedRAMP SAP template, which can be found on www.fedramp.gov/templates/.

3PAOs and independent assessors must abide by test case procedures found on www.fedramp.gov when assessing the CSP’s system.
Step 3:
Authorize
The independent assessor or C3PAO presents their findings via a Security Assessment Report (SAR), which should contain any discovered vulnerabilities, threats, and risks, as well as ways to mitigate these. The federal agencies that review the assessor’s findings may request further tests if risks were identified during the assessment stage. Otherwise, the federal agency may approve the report.
Key Points

In case risks were identified in the SAR, the CSP must present a Plan of Action & Motives (POA&M) that provides in detail how the security risks will be mitigated using available resources, staff, and an estimated completion schedule for remediation.
Step 4:
Continuous Monitoring
CSPs must continuously monitor their security controls and provide their findings to the authorizing agency. That means CSPs must be able to regularly scan their applications, databases, and servers for vulnerabilities. The C3PAO or independent assessor, for their part, should assess the CSP’s cloud security at least once a year.
Key Points

Continuous monitoring activities depend on what type of FedRAMP authorization the cloud provider wants to obtain. That means CSPs that want to provide services to multiple agencies require monthly and yearly assessments, while those that want to serve one or two may only require a yearly assessment.
What Is Microsoft GCC High?
Only DoD and Defense Industrial Base (DBI) contractors and federal agencies can use GCC High. Companies hoping to avail of GCC High services need to undergo Microsoft’s validation process.
GCC High is a cloud platform that meets the strict cybersecurity requirements of NIST 800-171, International Traffic in Arms Regulations (ITAR), and the Federal Risk and Authorization Management Program (FedRAMP). GCC High is a copy of Microsoft DoD, but the former is able to operate in its own sovereign environment.
GCC High comes with all the features found in the commercial version, except for compliance manager and calling plans. In addition, several tools including Cloud App Security, Microsoft Defender ATP, and if your company has a Microsoft 365 Commercial account and you want to take it up a notch and use GCC High, you need to go through several procedures to become a validated user.
To do this, you need to work with an Agreement for Online Services for Government (AOS-G) partner. An AOS-G partner is a managed IT services provider from whom you can purchase a Microsoft 365 license directly.
Do You Need GCC High to Be CMMC DoD Compliant?
This depends on the level of certification you are seeking.
GCC High is not included in the list of CMMC DoD compliance requirements for CMMC 2.0 Level 1 contracts. Even though it’s the only version of Microsoft 365 that complies with the reporting requirements stated in DFARS 7012, you do not need GCC High to get a CMMC 2.0 DoD certificate specifically for CMMC level 1.
However, if your organization is looking to become certified at level 2 or higher, there is a clause in the contract for DFARS 7012. Microsoft GCC High is the only reporting platform within Microsoft 365 and Office 365 that meets the requirements for DFARS 7012. Therefore, if your company is looking to become level 2 certified, and you use Office 365 or Microsoft 365, you will need GCC high to be compliant.
Back to top

05
Implementing a CMMC 2.0 Strategy
For contractors that need an audit, the process may be slow process for CMMC 2.0 certification. But this does not mean that all DoD contractors can do is wait until the accreditation board is ready to conduct audits. There are a number of ways contractors can ensure success in their upcoming certification by developing a clear compliance plan and strategy.
What Does the CMMC 2.0 Audit Look Like?

All contractors working for the DoD are required to be CMMC certified by passing a CMMC compliance audit. The CMMC Accreditation Body (AB) recommends that contractors should prepare for the audit at least six months in advance.

The DoD will work with certified third-party assessor organizations (C3PAOs) that will be responsible for performing audits to ensure a contractor has met all the required cybersecurity controls needed for a specific level.

A contractor will be level certified if the CMMC auditor sees it meets all the requirements specific to that level.
1
In-House
If your company has the available resources and IT staff, it can meet the CMMC 2.0 requirements without the help of a third-party consultant. A Self-Assessment Handbook – NIST Handbook 162 is available to guide your IT team, however, it only covers NIST SP 800-171 Rev. 1.
2
CMMC Consultant
A CMMC 2.0 consultant will help your company meet the controls stated in NIST Special Publication 800-172 In addition, many contractors prefer to have a consultant help them meet CMMC 2.0 requirements. Other benefits of having a CMMC 2.0 consultant are:

A consultant will save your company time and money when getting and maintaining compliance standards.

A CMMC consultant possesses the tools and documentation needed to conduct a gap analysis and create a system security plan.

A consultant can perform remediation steps required for compliance.

A consultant will have documents to prove that compliance is reached and maintained during a CMMC 2.0 audit.
Once your company is ready for a CMMC 2.0 audit or self-assessment, the first step is to perform a gap assessment. This assessment will determine how close or far away your company is from meeting CMMC 2.0 level standards. Other issues that gap assessments look for include:

How access to sensitive information is controlled and limited

How managers and systems administrators are trained

How data records are stored and protected from breaches

How security controls and policies are implemented

How cybersecurity incident response plans are created and implemented
A gap assessment with Charles IT will identify potential danger spots and weaknesses in your IT infrastructure. We then provide you with a remediation plan to address those weaknesses, ensuring a straight path to CMMC 2.0 compliance. Learn more about how a gap assessment can help you seal the cracks in your cybersecurity.
Steps to Success
No matter which route your company chooses, certain processes should be part of every CMMC 2.0 assessment or audit success strategy.

Step 1: Use existing guidelines to review your current cybersecurity maturity
Check your compliance with the Defense Federal Acquisition Regulation Supplement (DFARS), NIST SP 800-171, and NIST SP 800-172 regulations. This will give you a good baseline to see what controls you’ve implemented and which ones you might look to implement in the future. Level 2 CMMC 2.0 certification depends on NIST 800-171 security controls, so it’s a good way to start with DFARS compliance to evaluate your current compliance level with CMMC requirements.

Step 2: Identify the gaps in your security protocol and determine what needs to be strengthened or improved
Determine which security controls you need to implement, ideally after a gap assessment from a third party. Strengthen controls required for the CMMC 2.0 level you’re aiming to certify for. For most contractors with the DoD, that will be a level 2 certification, which allows handling of CUI.

Step 3: Assess your business’s ability to fill in the gaps (can you do it in house?)
Assess whether you’re fit to implement all needed security controls. Consider enlisting external help with critical services like endpoint encryption, external vulnerability scanning and backup and disaster recovery.

Step 4: Create a plan that will be sustainable in the long-term
Create a plan that clearly details company protocols, responsibilities of employees, the security solutions needed and their cost. With a detailed plan, you’ll be able to identify whether you have the manpower or budget to sustain the upgrades to your cybersecurity in the long-term. It will also help you decide whether it would be best for you to outsource these solutions or set them up yourself with your own resources.
Having a documented plan in the form of a POA&Ms is vital. Contractors that are not yet in full compliance with specified cybersecurity requirements may be permitted to perform less sensitive contracts with a detailed POA&M on record. Note that the DoD will provide a ruling on their time limits that will apply to these cases and is currently considering a 180-day timeline from contract award for companies to meet the measures laid out under their plans.

Step 5: Implement the plan and start step 1 again. (It’s a cycle after all!)
Check to see if the plans you’ve implemented actually got you closer to CMMC 2.0 compliance. You can do this by reviewing your refreshed cybersecurity protocols and identifying any further gaps that need to be filled.
Identifying and filling in gaps in your cybersecurity is an ongoing process. Merely implementing a group of security solutions won’t help to maintain CMMC 2.0 compliance. You and your team need to be informed and have access to proper channels of communication and support to ensure that your cybersecurity hygiene is operating at the optimum level.
To be fully prepared for your CMMC 2.0 audit or assessment, you’ll want to keep your eye on updates as the CMMC 2.0 process is rolled out. Appointing someone from your organization to be your designated CMMC 2.0 leader would be our recommendation. Your appointed leader will then be responsible for keeping up with updates, scrutinizing each area of your cybersecurity hygiene, and identifying your company’s preparedness for an audit or an assessment.
If you’re unsure whether a current employee has all the necessary expertise required to get your company certified, you can always consult with a trusted expert on CMMC regulations, like Charles IT.
Back to top

06
The Impact of Managed
Detection Response and SIEM
There are additional layers of security that many contractors opt to implement. Managed Detection and Response (MDR) is an advanced approach to managing cybersecurity challenges through the proactive detection of potentially malicious activities across a network. It’s a type of outsourced service that provides organizations access to the tools and knowledge they need to achieve a high level of cybersecurity maturity even if they have limited in-house resources.
In addition, SIEM tools, which typically take the form of outsourced, cloud-hosted platforms, play a central role in any modern cybersecurity strategy. Newer solutions make extensive use of machine learning and artificial intelligence to aggregate and analyze data at a scale that is practically impossible to accomplish by people alone.
MDR Explained
Although there’s some overlap, in general, between MDR and managed security services, there are some important differences regarding coverage, compliance, incident response, detection levels, and human expertise. Modern threat detection services, for example, use behavioral AI to recognize potentially malicious activities regardless of their origins and attack vectors. A response program proactively manages and reverses malicious activities so every endpoint can be healed in real time.
Proactive detection and response are core concepts of CMMC 2.0. Higher levels of CMMC 2.0 compliance, in particular, require systems and practices to be put into place that enhance detection and response capabilities of an organization so they can adapt to evolving tactics, techniques, and procedures used in cyberattacks.
Achieving a CMMC 2.0 level 2 or 3 certification might seem like a daunting task. It requires a deep understanding of your IT systems and processes, and the threat models and vectors that criminals and state-sponsored attackers use when they try to compromise your systems. However, reaching this level can greatly expand your business’s chances of securing profitable contracts with the DoD.
It’s almost impossible for all but the largest enterprises to achieve a high cybersecurity maturity without external help. Even in cases where money isn’t a factor, there are millions of unfilled information security positions around the world. Simply put, in most cases, outsourcing is the only practical option.
Outsourcing isn’t just a necessity in many cases, MDR can also be highly beneficial to the long-term mission of a business. It allows businesses to innovate at scale, without increasing risk, while also becoming more resilient to change, especially with regard to the cyberthreat landscape.
MDR is now an essential extra layer of security, not just for those seeking CMMC 2.0 certification, but also for reducing risk to their business and clients. By contrast, traditional managed security services only provide a base level in the form of event logging and monitoring, device scanning, and policy management.
SIEM Explained
While CMMC 2.0 is clear on precisely which controls you need to have in place to reach a higher security level, exactly how you implement them and which tools and services you use is up to you. But keep in mind that Level 2 of CMMC 2.0 security introduces log collection and analysis, which serve as important first steps in achieving proactive security.
SIEM services offer three primary capabilities – threat detection, investigation, and alerting. Additional features, such as forensics and incident response, and log collection are also highly important. The key element here is the collective management of audit logs, simply because managing logs across multiple disparate systems makes it near impossible to correlate between events from various systems. Implementing a SIEM solution is a major step towards achieving CMMC 2.0 compliance and enhancing your overall security posture.
Back to top
Conclusion
Your company’s ability to conduct business with the DoD is on the line if you don’t pass your CMMC 2.0 audit or demonstrate adequate annual self-assessments. If you handle CUI, then you’ll need to get that certification on your first CMMC 2.0 audit, so you don’t lose critical time and revenue preparing for and conducting reassessments.
This means that CMMC 2.0 preparations should start as soon as possible. The sooner an organization begins preparation, the more efficiently they can assess the gaps in their current cybersecurity hygiene. Remember, self-certification is only an option for Level 1 contractors, and in limited instances for level 2. DoD CMMC 2.0 certification can only be awarded upon a positive review by an accredited third-party C3PAO auditor.
DoD contractors shouldn’t view CMMC 2.0 compliance as something that’s complete once they’ve passed an audit. Instead, it should be approached as a starting point for iteratively improving your organization’s cybersecurity posture. Building a security-first company culture will add value throughout the business and open the doors to innovation. Becoming certified and working your way up through the levels will ensure that you’re better positioned to compete in a highly lucrative market.
The easiest way to prepare for CMMC 2.0 compliance is to work with a CMMC consultant, especially if you don’t have access to the necessary in-house expertise. For many contractors, it makes more sense to outsource the task, since it costs less, saves time, and ensures that the necessary requirements have been met before an official audit.
Table of Contents
Main Menu

Save it for later. Download the PDF version of this ebook!

